Lets say you download a file from internet and you want to make sure that this file’s source is legitimate (say you just downloaded new ISO of Ubuntu from their site). Or in another case you want to make sure that there is no corruption in file that you just downloaded from internet (now you may argue that why bother ? Can’t you just download that file again ? … but sometimes it’s not that simple … and that’s how it works in office bureaucracy ![]() ) … in both of these cases usually you can ask for hash key generated using either MD5 or SHA-1 algorithms from person who sent you that file and compare those keys with key generated by you and if that matches then everything is good … and if it doesn’t then something funny is going on. In fact, today it is very common practice by many companies to provide MD5 and/or SHA-1 hash keys for their software to make sure that they are not tempered with.
) … in both of these cases usually you can ask for hash key generated using either MD5 or SHA-1 algorithms from person who sent you that file and compare those keys with key generated by you and if that matches then everything is good … and if it doesn’t then something funny is going on. In fact, today it is very common practice by many companies to provide MD5 and/or SHA-1 hash keys for their software to make sure that they are not tempered with.
And File Checksum Integrity Verifier aka FCIV is a mouthful name of a tiny utility by MSFT. Sole purpose of this utility is to create or compare file integrity using MD5 or SHA-1 hashing algorithms. First step for that is of course to get FCIV from MSFT Download Center. Only issue (!!) is there is no GUI for this utility, so you will need to use terminal to run this utility.
Following is copy from help of this tool,
//
// File Checksum Integrity Verifier version 2.05.
//Usage: fciv.exe [Commands] <Options>
Commands: ( Default -add )
-add <file | dir> : Compute hash and send to output (default screen).
dir options:
-r : recursive.
-type : ex: -type *.exe.
-exc file: list of directories that should not be computed.
-wp : Without full path name. ( Default store full path)
-bp : specify base path to remove from full path name-list : List entries in the database.
-v : Verify hashes.
: Option: -bp basepath.-? -h -help : Extended Help.
Options:
-md5 | -sha1 | -both : Specify hashtype, default md5.
-xml db : Specify database format and name.To display the MD5 hash of a file, type fciv.exe filename
So, to generate MD5 or SHA-1 for any file just run following command,
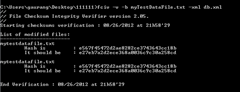
fciv -both myTestDataFile.txt -xml db.xml
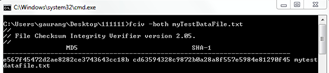 |
This will generate both MD5 and SHA-1 hash keys for myTestDataFile and stores both keys it into XML database. Now if you compare this generated key with key of the file using following command,
fciv –v -both myTestDataFile.txt -xml db.xml
You will see that it will match successfully because there is no modification to file is done after keys were generated.
Now, say for example you modify this file to simulate unapproved changes and now compare this file’s MD5 or SHA-1 hash keys with that XML database from file before modification using same command, you will see that verification fails this time because file is modified after keys were generated.
I find this tool particularly useful to verify integrity of a file downloaded from internet. Specially in a case when you want to be sure that if you are having some issue with that file then is it because of crappy application or it’s because of your crappy computer ![]()
That’s it for now…
It’s Just A Thought … ![]()